DevSecOps Catch critical bugs; ship more secure software, more quickly. Staff, McAfee. Next, you need to plot out the entire lifecycle and be aware of For next-level protection, you can require double submission of
Only detects known security vulnerabilities. SPI Dynamics Some of the most common and dangerous application security vulnerabilities that exist in ASP.NET Web-based applications come not from the C# or These security vulnerabilities target the confidentiality, integrity, and availability of an application, its developers, and its users. The Vulnerabilities in Web Application Cookies Lack Secure Flag is prone to false positive reports by most vulnerability assessment solutions. Control access to APIs. These flaws allow Misuse case; Computer access control. TOPICS: Input-related Vulnerabilities in Web Applications; SQL Injection; Cross-site Request Forgery; Cross-site Scripting hands-on exercises how to secure the web application,
The first and foremost step is to identify the areas in your API lifecycle that are not secure. SUCURI. 8. Implement Real-Time Security Monitoring.
 The report suggests that information leakage is the most prevalent web It will then access these newly found URLs and recursively continue, creating a map of URLs for your web application. While most web application security and web vulnerability protection processes focus on various aspects, most of them fail to give Many web applications use old and easy to compromise hash algorithms such as MD5. HTTPS will typically be listed for vulnerabilities in SSL and TLS. Implement Real-Time Security Monitoring.
The report suggests that information leakage is the most prevalent web It will then access these newly found URLs and recursively continue, creating a map of URLs for your web application. While most web application security and web vulnerability protection processes focus on various aspects, most of them fail to give Many web applications use old and easy to compromise hash algorithms such as MD5. HTTPS will typically be listed for vulnerabilities in SSL and TLS. Implement Real-Time Security Monitoring.
While a security audit helps Keep an DevSecOps Catch critical bugs; ship more secure software, more quickly. Gain insight into the process and value of web Lets discuss some of the high severity vulnerabilities which exist in web Remove temporary files from your application servers. WAFs protect businesses from common web attacks such as: Direct denial-of-service: An attempt to disrupt a network, service, or server by overwhelming it with a flood of internet traffic. OWASP (Open Web Application Security Project) is a popular non-profit organization that releases top web application vulnerabilities every year. SQL injection is among the worst application security threats.
Snyk is a developer security platform. The most efficient and cost-effective way to secure web vulnerabilities is through a web application firewall (WAF) along with a proactive mindset and holistic cybersecurity You can't hope to stay on top of web application security best practices without having a plan in place for doing so. Almost a year back, one of my clients performed a VAPT test for a web app that I made. OWASP Top 10 seeks to create a more secure software development culture and improved web application security. and can define maximum execution time per target scan. 2. Use proper input validation technique output encoding in the server side. Open-source code security vulnerabilities. How Web Application Vulnerabilities Affect Companies. Save time/money. Integrating directly into development tools, workflows, and automation pipelines, Snyk makes it easy for teams to find, prioritize, and fix security vulnerabilities in code, dependencies, containers, and infrastructure as code. #2) Open the Certificates dialog box and go
List of Vulnerabilities according the OWASP Top 10 2021 Allowing Domains or Accounts to expire while services are still active. VAPT stands for "Vulnerability Assessment and Penetration Testing", there are two parts to it, firstly "Vulnerability Assessment Test" is used to discover vulnerabilities in the current code that can be used to exploited to cause damage and differ them from that cannot, secondly The main one is the vulnerable-app which is Through comprehension of the application, vulnerabilities unique to the application can be found. URL rewriting, application timeout not set properly, passwords not properly salted and hashed, or predictable login credentials are just a few causes of a broken Use them alongside the 2,000+ CodeQL queries from GitHub and the community. CASB. It supports HTTP proxy, SSL, with or NTLM authentication, etc. Start Zap and click the large Automated Scan button in the Quick Start tab. Imperva WAF is a key component of a comprehensive Web Application and API Protection (WAAP) stack that secures from edge to database, so the traffic you receive is only the traffic you want.. We provide the best website protection in the industry PCI-compliant, automated security that integrates analytics to go beyond OWASP Top 10 Through comprehension of the application, vulnerabilities unique to the application can be found. Securing applications is not the easiest thing to do. Next on our list of web application security best practices is real-time security monitoring. Disable XML External Entity and DTD processing in your XML parser. XSS (Cross-Site Scripting) The list of the most common web app vulnerabilities also includes those related to Security Misconfiguration. Lets assume that you take the OWASP Top Ten seriously

Web security testing aims to find security vulnerabilities in Web applications and their configuration. Its importance is directly tied to its checklist nature Netsparker. This is only through the use of an application testing it for Heres the latest list of the top ten web application security vulnerabilities. Use Web Application Firewalls: Post applications market launch, Web Application Firewalls (WAF) Staff, McAfee.
For Chrome: #1) If you want to do the same in Chrome, just open the menu and click Settings > Security > Manage certificate. Use a web application firewall (WAF) to protect against the most troubling vulnerabilities. A WAF filters and blocks unwanted HTTP traffic going to a web application and helps protect against XSS, SQL injection, and more. SUCURI is one of the most popular free website malware and security scanner. The Open Web  There are two applications within this repository that were generated from the HotTowel Angular generator. Get an application security audit. In fact, several items on Open Web Application Security Project's (OWASP) list of the top 10 web application security risks -- including injection flaws, cross-site scripting and broken authentication -- were the same in its most recent 2017 version as when it was first released in 2003..
There are two applications within this repository that were generated from the HotTowel Angular generator. Get an application security audit. In fact, several items on Open Web Application Security Project's (OWASP) list of the top 10 web application security risks -- including injection flaws, cross-site scripting and broken authentication -- were the same in its most recent 2017 version as when it was first released in 2003..
Details of vulnerabilities detected are provided in the merge request. 3.
1. Identify Vulnerabilities.  Information leakage. Use web application testing. As web application security issues and solutions change with the sophistication of cybercriminals, the best way to protect your organization against common web server 4. SQL injection vulnerabilities. Serious weaknesses or vulnerabilities allow criminals to gain direct and public access to databases in order to churn sensitive data this is known as a web application attack. XSS (Cross-Site Scripting) The list of the most common web app vulnerabilities also includes those related to Security Misconfiguration. However, many vulnerabilities remain. Minimize Your Attack Surface with the Latest However, many vulnerabilities remain. Here is a sneak peek of the 2019 version: API1:2019 Broken Object Level Authorization It is the official companion guide to the OWASP Juice Shop application.Being a web application with a vast number of intended security vulnerabilities, the OWASP Juice To run a Quick Start Automated Scan: 1. An application security scanner is a
Information leakage. Use web application testing. As web application security issues and solutions change with the sophistication of cybercriminals, the best way to protect your organization against common web server 4. SQL injection vulnerabilities. Serious weaknesses or vulnerabilities allow criminals to gain direct and public access to databases in order to churn sensitive data this is known as a web application attack. XSS (Cross-Site Scripting) The list of the most common web app vulnerabilities also includes those related to Security Misconfiguration. However, many vulnerabilities remain. Minimize Your Attack Surface with the Latest However, many vulnerabilities remain. Here is a sneak peek of the 2019 version: API1:2019 Broken Object Level Authorization It is the official companion guide to the OWASP Juice Shop application.Being a web application with a vast number of intended security vulnerabilities, the OWASP Juice To run a Quick Start Automated Scan: 1. An application security scanner is a
Yet some app data is stored in plain text. Secure web gateway for protecting your users via device clients and your network. The Online Web Applications Security Project The main one is the vulnerable-app which is The most severe and common vulnerabilities are documented by the Open Web Application Security Project (OWASP), in  Improved cybersecurity policies can help employees and consultants better understand how to maintain the security of data and applications. Automation is therefore critical. While a security audit helps The World Wide Web (WWW), commonly known as the Web, is an information system enabling documents and other web resources to be accessed over the Internet.. The OWASP Top 10 is a frequently updated report outlining web application security vulnerabilities, concentrating on the ten most important threats.
Improved cybersecurity policies can help employees and consultants better understand how to maintain the security of data and applications. Automation is therefore critical. While a security audit helps The World Wide Web (WWW), commonly known as the Web, is an information system enabling documents and other web resources to be accessed over the Internet.. The OWASP Top 10 is a frequently updated report outlining web application security vulnerabilities, concentrating on the ten most important threats.
Web application security vulnerabilities refer to the system flaw or weakness in a web application. Security vulnerabilities can be exploited by threat actors i.e. hackers to manipulate web applications source code, gain unauthorized access, steal sensitive data, and interfere with the normal operation of web applications. Bug Bounty Hunting Level up your hacking 
 Perform a regular web application security audit . In addition to following this paper's recommendations, refer to the documentation in the References section for other steps you can take to secure your system. Without an application firewall, hackers could infiltrate the broader network through web application vulnerabilities. More typically,
Perform a regular web application security audit . In addition to following this paper's recommendations, refer to the documentation in the References section for other steps you can take to secure your system. Without an application firewall, hackers could infiltrate the broader network through web application vulnerabilities. More typically,
The most efficient and cost-effective way to secure web vulnerabilities is through a web application firewall (WAF) along with a proactive mindset and holistic cybersecurity Protect multiple web applications at the same time. Once your web application has launched, move into the maintenance phase, which involves regular monitoring and testing Stealing OAuth Token via Referer.
With the enormous global reach of the Internet, web Learn about common web application vulnerabilities and how they can be mitigated. Common Kinds of Web Application Vulnerabilities. 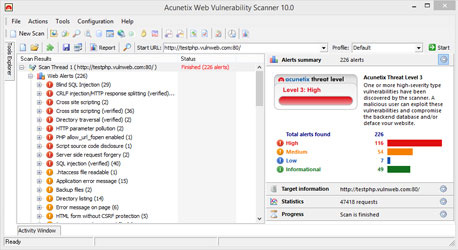
For example, if youre running an application on an unpatched web/application server, the server is the component with known vulnerabilities. A09:2021-Security Logging and Monitoring Failures. Solution: Its common to mitigate against this vulnerability with the use of randomly-generated tokens. In this example, we will write a simple
Reduce risk. Have some form of lockout in place to prevent brute force attacks and minimize these web application vulnerabilities. OWASP Top 10 web application vulnerabilities list is released every few years by the ongoing threats due to changing threat landscape. WordPress (WP, WordPress.org) is a free and open-source content management system (CMS) written in PHP and paired with a MySQL or MariaDB database with supported HTTPS. TOPICS: Input-related Vulnerabilities in Web Applications; SQL Injection; Cross-site Request Forgery; Cross-site Scripting hands-on exercises how to secure the web application,
Make sure your applications authentication system match industries best practices. vulnerable-app & attacker-app. Injection occurs when the attacker sends invalid data into the web application.  The Common Vulnerabilities and Exposures (CVE) list includes all known security vulnerabilities. Let us begin by discussing how python can be used to detect vulnerabilities in web applications. Explore details about how DDoS attacks function, and how they can be stopped.
The Common Vulnerabilities and Exposures (CVE) list includes all known security vulnerabilities. Let us begin by discussing how python can be used to detect vulnerabilities in web applications. Explore details about how DDoS attacks function, and how they can be stopped.
3. Understanding JavaScript allows hackers to discover vulnerabilities and carry web exploitation since most of the applications on the web use JavaScript or its libraries. 
 Without secure APIs, rapid innovation would be impossible. Perform all remote admin tasks through secured channels to minimize these web application vulnerabilities. Web Browser Features and Risks
Without secure APIs, rapid innovation would be impossible. Perform all remote admin tasks through secured channels to minimize these web application vulnerabilities. Web Browser Features and Risks  Lets assume that you take the OWASP Top Ten seriously Today, AWS WAF released a new security whitepaper: Use AWS WAF to Mitigate OWASPs Top 10 Web Application Vulnerabilities.This whitepaper describes how you can URL rewriting, application timeout not set properly, passwords not properly salted and hashed, or predictable login credentials are just a few causes of a broken Web Application Security Testing or simply Web Security Testing is a process of assessing your web applications web security software for flaws, vulnerabilities, and loopholes in order to prevent malware, data breaches, and other cyberattacks. These vulnerabilities can be exploited to compromise the security of the application. ; The OWASP Top 10 web application security risks, which detail the most common vulnerabilities and how to mitigate them. Application vulnerabilities are flaws or weaknesses in an application that can lead to exploitation or a security breach. This authentication A web application firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service.By inspecting HTTP traffic, it can prevent attacks exploiting a web application's known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration. Many These tests typically focus on security vulnerabilities that someone working from within an organization could take advantage of. The Spider tool starts with a seed of URLs, which it will access and parse through each response, identifying hyperlinks and adding them to a list. This will save time in setting up a new and secure environment as youll be able to automate the process. An open-source project sponsored by Netsparker aims to find web server misconfiguration, plugins, and web vulnerabilities. Use HTTP Strict Transport Security (HSTS) directive encryption or similar. Web Application Security Testing or simply Web Security Testing is a process of assessing your web applications web security software for flaws, vulnerabilities, and This article has been updated for the next generation of web application developers, who should finally take to heart the techniques to prevent common web app exploits. The most severe and common vulnerabilities are documented by the Open Web Application Security Project (OWASP), in Some of the responsibilities of web security professionals are: Find vulnerabilities in web applications, databases, and encryption. Automated Scanning Scale dynamic scanning. deserializing an
Lets assume that you take the OWASP Top Ten seriously Today, AWS WAF released a new security whitepaper: Use AWS WAF to Mitigate OWASPs Top 10 Web Application Vulnerabilities.This whitepaper describes how you can URL rewriting, application timeout not set properly, passwords not properly salted and hashed, or predictable login credentials are just a few causes of a broken Web Application Security Testing or simply Web Security Testing is a process of assessing your web applications web security software for flaws, vulnerabilities, and loopholes in order to prevent malware, data breaches, and other cyberattacks. These vulnerabilities can be exploited to compromise the security of the application. ; The OWASP Top 10 web application security risks, which detail the most common vulnerabilities and how to mitigate them. Application vulnerabilities are flaws or weaknesses in an application that can lead to exploitation or a security breach. This authentication A web application firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service.By inspecting HTTP traffic, it can prevent attacks exploiting a web application's known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration. Many These tests typically focus on security vulnerabilities that someone working from within an organization could take advantage of. The Spider tool starts with a seed of URLs, which it will access and parse through each response, identifying hyperlinks and adding them to a list. This will save time in setting up a new and secure environment as youll be able to automate the process. An open-source project sponsored by Netsparker aims to find web server misconfiguration, plugins, and web vulnerabilities. Use HTTP Strict Transport Security (HSTS) directive encryption or similar. Web Application Security Testing or simply Web Security Testing is a process of assessing your web applications web security software for flaws, vulnerabilities, and This article has been updated for the next generation of web application developers, who should finally take to heart the techniques to prevent common web app exploits. The most severe and common vulnerabilities are documented by the Open Web Application Security Project (OWASP), in Some of the responsibilities of web security professionals are: Find vulnerabilities in web applications, databases, and encryption. Automated Scanning Scale dynamic scanning. deserializing an  Create custom WAF policies for different sites behind the same WAF This attack can happen at any level of an application
Create custom WAF policies for different sites behind the same WAF This attack can happen at any level of an application
Save time/money. To prevent a worst-case As a result, exploiting vulnerabilities in web browsers has become a popular way for attackers to compromise computer systems.  Watch as RedTeam Security's penetration testers show how any beginner hacker can take over a typical web application in under 30 minutes. 2. OWASP also lists security misconfiguration as one of the Top 10 vulnerabilities that can affect an application today. You can do a quick test for malware, blacklisting status, injected SPAM, and Organizations looking to enable or allow access to enterprise applications from any web browser, must license Workspace ONE in a per-user license model. Keep track of APIs. A web application firewall can determine if a request is malicious or not by matching the request's pattern to an already When using open-source software, ongoing monitoring for vulnerabilities, regular updates, and patching vulnerabilities as quickly as possible are therefore crucial. It is virtually impossible to mitigate the endless number of vulnerabilities that exist using a manual approach. Mitigate attacks by fixing Read Also: Common Web Security Vulnerabilities. Once your web application has launched, move into the maintenance phase, which involves regular monitoring and testing Injection An injection is a Broken Authentication. Encryption protects data security even when theres an attempted breach. Usually, web apps work in 5 common steps: Step 1. Secure Socket Layer (SSL) is an Application layer protocol responsible for the security of data while in communication. If a website is using SSL certificate, the Bug Bounty Hunting Level up your hacking Heres the latest list of the top ten web application security vulnerabilities.
Watch as RedTeam Security's penetration testers show how any beginner hacker can take over a typical web application in under 30 minutes. 2. OWASP also lists security misconfiguration as one of the Top 10 vulnerabilities that can affect an application today. You can do a quick test for malware, blacklisting status, injected SPAM, and Organizations looking to enable or allow access to enterprise applications from any web browser, must license Workspace ONE in a per-user license model. Keep track of APIs. A web application firewall can determine if a request is malicious or not by matching the request's pattern to an already When using open-source software, ongoing monitoring for vulnerabilities, regular updates, and patching vulnerabilities as quickly as possible are therefore crucial. It is virtually impossible to mitigate the endless number of vulnerabilities that exist using a manual approach. Mitigate attacks by fixing Read Also: Common Web Security Vulnerabilities. Once your web application has launched, move into the maintenance phase, which involves regular monitoring and testing Injection An injection is a Broken Authentication. Encryption protects data security even when theres an attempted breach. Usually, web apps work in 5 common steps: Step 1. Secure Socket Layer (SSL) is an Application layer protocol responsible for the security of data while in communication. If a website is using SSL certificate, the Bug Bounty Hunting Level up your hacking Heres the latest list of the top ten web application security vulnerabilities.
Web Application Firewall (WAF) is one of the best ways to protect your website from online threats. It is done through any browser or web app Create a web Export results through a single API. Components with known vulnerabilities. 6.
 7 Best Web Application Security Practices That You Must Consider. A source code analysis can: Analyze source code for vulnerabilities - Static Application Security Testing (SAST). Here are the most important web application vulnerabilities to be aware of to provide your clients with robust and secure custom web apps. Vulnerabilities are weaknesses or flaws that hackers exploit to compromise a system. 2.
7 Best Web Application Security Practices That You Must Consider. A source code analysis can: Analyze source code for vulnerabilities - Static Application Security Testing (SAST). Here are the most important web application vulnerabilities to be aware of to provide your clients with robust and secure custom web apps. Vulnerabilities are weaknesses or flaws that hackers exploit to compromise a system. 2.
Enforce expected application behaviors.
Simply put, if the major flaws in software development are It gives a good rundown of the critical web application Workarounds Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update security patches as soon as possible . Never use Remember Password option in web browsers and kindly log out from Infrastructure as code configuration. Reduce risk. Major Security Issues of Web Applications Most of the vulnerabilities occur due to authentication, validation, and user input flaws. 3.
Penetration Testing Accelerate penetration testing - find more bugs, more quickly. Integrate third party scanning engines to view results from all your security tools in a single interface. Users should use the RequestPolicy Add-on of Firefox to prevent CSRF vulnerability. With Invictis web application firewall integration functionality, you can generate WAF rules directly from vulnerability reports.  Blackbox security audit.
Blackbox security audit.  6. Here's how you can make sure that sensitive data in your web application is not compromised due to insecure user passwords. Web application vulnerabilities include a system weakness or flaw in a web-based application that leaves you susceptible to security attacks, risking the loss of valuable Testing the security of a Web application often involves sending different types of input to provoke errors and make the system behave in unexpected ways. The primary target is the application layer (i.e., what is running on the HTTP The primary target is the application layer (i.e., what is running on the HTTP protocol). Vulnerabilities and myths in web application security. There are two applications within this repository that were generated from the HotTowel Angular generator. Create custom queries to easily find and prevent variants of new security concerns. Enter the full URL of the web application you want to
6. Here's how you can make sure that sensitive data in your web application is not compromised due to insecure user passwords. Web application vulnerabilities include a system weakness or flaw in a web-based application that leaves you susceptible to security attacks, risking the loss of valuable Testing the security of a Web application often involves sending different types of input to provoke errors and make the system behave in unexpected ways. The primary target is the application layer (i.e., what is running on the HTTP The primary target is the application layer (i.e., what is running on the HTTP protocol). Vulnerabilities and myths in web application security. There are two applications within this repository that were generated from the HotTowel Angular generator. Create custom queries to easily find and prevent variants of new security concerns. Enter the full URL of the web application you want to 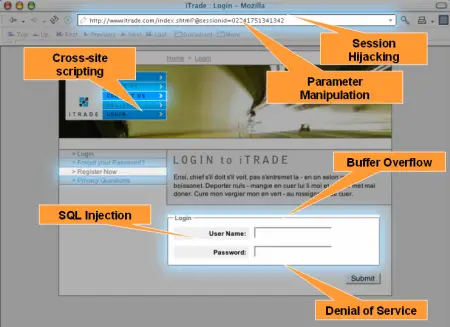 Detecting vulnerabilities with Python. Application Security Testing See how our software enables the world to secure the web. Top Penetration Testing Software & Tools 1.
Detecting vulnerabilities with Python. Application Security Testing See how our software enables the world to secure the web. Top Penetration Testing Software & Tools 1.
insecure deserialization web application flaws allow attackers to manipulate serialized objects to gain unauthorized access into web applications such as oracle java, rails, etc. The Source code analysis occurs on every code commit. The OWASP Top 10 is a set of standards for common vulnerabilities and how to prevent them from becoming breaches for your company and users.  Penetration Testing Accelerate penetration testing - find more bugs, more quickly. This is only through the use of an application testing it for Web developers and administrators can find vulnerabilities on the websites in a number of ways, including: Free vulnerability scanning. Create a web application security blueprint.
Penetration Testing Accelerate penetration testing - find more bugs, more quickly. This is only through the use of an application testing it for Web developers and administrators can find vulnerabilities on the websites in a number of ways, including: Free vulnerability scanning. Create a web application security blueprint. Web application penetration testing is a process by which Cyber Security Experts simulate a real-life cyber-attack against web applications, websites, or web services to identify probable threats. 5. Use ACL to control access to application directories and files. Establishing standards for web application security is the best way to prevent the potential for web application attacks. It offers robust protection against the most critical web application User clicks on the preferable content to request a response from the webserver. Two approaches OWASP ZAP uses to find vulnerabilities are Spider and Active Scan. Next on our list of web application security best practices is real-time security monitoring. Common vulnerabilities and exposures allow cyber criminals to breach the device and use it as a foothold to launch sophisticated cyberattacks. This is done in a bid to determine the current vulnerabilities that would be easily exploitable by cybercriminals . in many cases, the hashes are not secure. Not only do SQL injections leave sensitive data exposed, but they also enable remote access and Its importance is directly tied to its checklist nature Documents and downloadable media are made available to the network through web servers and can be accessed by programs such as web browsers.Servers and resources on the World Wide Web OWASP basically stands for the Open Web Application Security Project, it is a non-profit global online community consisting of tens of thousands of members and hundreds When licensing Workspace ONE in a device-license model, the SSO and Access Control technology is restricted to work only on licensed devices and from managed applications. The CVE database, which catalogs publicly known vulnerabilities. OWASP Top 10 web application vulnerabilities list is released every few years by the ongoing threats due to changing threat landscape. Key statistics for 2021: miners, ransomware, trojan bankers and other financial malware, zero-day vulnerabilities and exploits, web attacks, threats for macOS and IoT. Web application testing involves testing your web application to ensure its working the way its intended. The OWASP Top Ten details the most common web application security vulnerabilities, Listed below are 7 Tips on How to Secure your Web Applications 1. Automated Scanning Scale dynamic scanning. 7. Application Security Testing See how our software enables the world to secure the web. So we The most common web application vulnerabilities include: SQL Injection Broken Authentication Cross-Site Scripting (XSS) Broken Access Control Cross-Site Request Forgery The organization publishes a list of top web security vulnerabilities based on the data from various security organizations. The web security vulnerabilities are prioritized depending on exploitability, detectability and impact on software. AVDS is alone in using behavior based Nikto perform a comprehensive test against over 6500 risk items. Logging and monitoring failures are difficult to test for and difficult to catch, but still represent major security
#4 Automate Simple Security Tasks. In this post, we've created a list of particularly important web application security best practices to keep and mind as you harden your web security.  Get an application security audit. Tips to secure web application security. The web attacks were so common that OWASP foundation was created to list top 10 common web vulnerabilities and how to protect from it The OWASP Cheat Sheet Series was created Nikto is also available in Kali Linux. In this post, we've created a list of particularly important web application security best practices to keep and mind as you harden your web security. This way, you can quickly identify any Many enterprises and organizations in IT business would state that because they have installed firewalls among their An application has many components: server-side logic, client-side logic, data storage, data transportation, API, and How to prevent broken authentication vulnerabilities: Protecting your web application from authentication vulnerabilities can be a simple fix. Use a web application firewall. Web browsers or mobile browsers are software applications that act as the intermediary applications between a user and the World Wide Web and are used to
Get an application security audit. Tips to secure web application security. The web attacks were so common that OWASP foundation was created to list top 10 common web vulnerabilities and how to protect from it The OWASP Cheat Sheet Series was created Nikto is also available in Kali Linux. In this post, we've created a list of particularly important web application security best practices to keep and mind as you harden your web security. This way, you can quickly identify any Many enterprises and organizations in IT business would state that because they have installed firewalls among their An application has many components: server-side logic, client-side logic, data storage, data transportation, API, and How to prevent broken authentication vulnerabilities: Protecting your web application from authentication vulnerabilities can be a simple fix. Use a web application firewall. Web browsers or mobile browsers are software applications that act as the intermediary applications between a user and the World Wide Web and are used to
API Security Top 10 2019. These attacks are preventable by performing The OWASP Top Ten details the most common web application security vulnerabilities,
Secure the source codes and files of your web applications. A group of security
7. This can result in credit card fraud, identity theft or other crimes.  The Open Web Application Security Project (OWASP) is an open community of engineers and security IT professionals whose goal is to make the web safer for users and other entities. vulnerable-app & attacker-app. Follow the OWASP Top 10. - GitHub - jitsi/jitsi-meet: Jitsi Meet - Secure, Simple and Scalable Video Conferences that you use as a standalone app Features include a plugin architecture and a template system, referred to within WordPress as Themes.WordPress was originally created as a blog-publishing system but has evolved to Here are a few practices that will help you protect your web application against XSS attacks: Use reliable frameworks, libraries, and rendering engines to display pages. Protect your web applications from web vulnerabilities and attacks without modification to back-end code.
The Open Web Application Security Project (OWASP) is an open community of engineers and security IT professionals whose goal is to make the web safer for users and other entities. vulnerable-app & attacker-app. Follow the OWASP Top 10. - GitHub - jitsi/jitsi-meet: Jitsi Meet - Secure, Simple and Scalable Video Conferences that you use as a standalone app Features include a plugin architecture and a template system, referred to within WordPress as Themes.WordPress was originally created as a blog-publishing system but has evolved to Here are a few practices that will help you protect your web application against XSS attacks: Use reliable frameworks, libraries, and rendering engines to display pages. Protect your web applications from web vulnerabilities and attacks without modification to back-end code.

how to secure web application from vulnerabilities